Introduction
 Welcome to loxilb documentation
Welcome to loxilb documentation
Background
loxilb began as a project to simplify the deployment of cloud-native and Kubernetes workloads at the edge. In public cloud environments like AWS or GCP, exposing services to the outside world is often effortless. These platforms typically provide external load balancers by default, ensuring smooth and efficient handling of inbound traffic.
In contrast, on-premise and edge deployments face a different challenge. There’s no native equivalent of the ServiceType=LoadBalancer in these environments. For a long time, MetalLB was the only practical option. However, edge workloads come with their own unique set of complexities. These workloads frequently rely on specialized protocols like QUIC, SCTP, and SRv6, and they operate under tighter latency budgets and stricter resource constraints. Building a seamless and reliable solution in such an environment requires deep protocol awareness and careful design.
As more users approached us to solve these challenges, it became clear that the traditional Linux networking stack, while mature and reliable, lacked the agility to rapidly support the wide variety of protocols and stateful load-balancing scenarios needed at the edge.
This led us to adopt eBPF, a powerful technology from the Linux community. eBPF enables safely running sandboxed programs within the kernel, allowing us to extend system functionality without altering kernel source code or introducing performance overhead. It provides the flexibility and performance essential for modern networking use cases — without requiring dedicated CPU cores — making it an ideal foundation for lightweight, energy-efficient edge architectures.
What is loxilb
loxilb is an open-source, cloud-native load balancer built using Go and eBPF, designed to offer seamless cross-compatibility across on-premise, public cloud, and hybrid Kubernetes environments.
Its primary goal is to enable efficient and flexible load balancing for next-generation workloads, especially in complex deployment scenarios. Whether it's telecom, mobility, or edge computing, loxilb is built to support the growing adoption of cloud-native technologies in these demanding sectors.
By leveraging the power of eBPF, loxilb delivers high-performance networking with deep protocol awareness, minimal resource overhead, and a modern, extensible design. This makes it an ideal fit for both traditional and emerging infrastructure needs.
Kubernetes with loxilb
Kubernetes defines several service constructs such as ClusterIP, NodePort, LoadBalancer, and Ingress to handle different types of communication — from pod-to-pod and pod-to-service, to service access from the outside world.
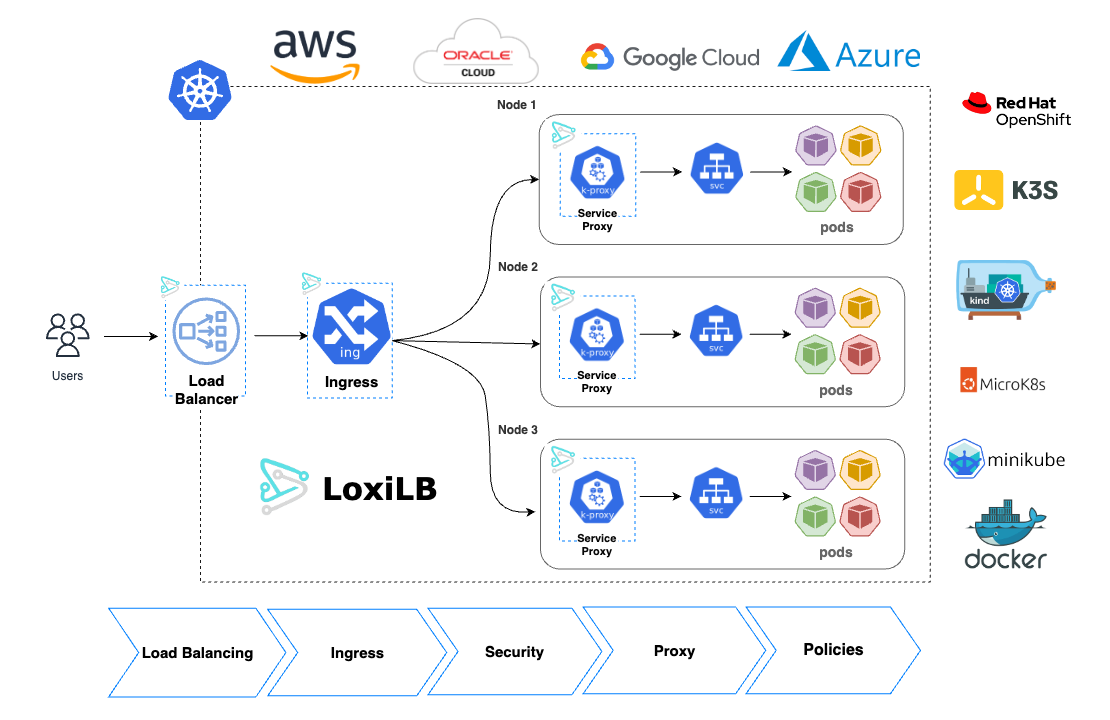
All of these service types rely on load balancers or proxies operating at Layer 4 or Layer 7. Thanks to Kubernetes’ modular architecture, these services can be delivered by different software components. For instance, kube-proxy is commonly used to provide ClusterIP and NodePort functionality. However, for services like LoadBalancer and Ingress, Kubernetes typically does not include a default provider.
The LoadBalancer service type is usually managed by public cloud providers as part of their infrastructure. In on-premise or self-managed clusters, there are limited options available. Even in managed Kubernetes environments like Amazon EKS, many users prefer to bring their own load balancer for more control, customization, or advanced protocol support.
This need becomes even more critical in domains like 5G telco and edge computing, where protocols such as QUIC, GTP, SCTP, SRv6, SEPP, and DTLS are involved. These use cases introduce complex requirements that demand flexibility and high performance. loxilb is designed to meet these challenges, with support for the LoadBalancer service type as a core capability. It can be deployed either within the cluster or externally, depending on user requirements.
By default, loxilb acts as a Layer 4 load balancer and service proxy. While L4 load balancing offers high performance and broad protocol coverage, Kubernetes also benefits from robust Layer 7 capabilities. loxilb supports L7 load balancing through its Ingress implementation, which is enhanced using eBPF sockmap helpers. This makes it a strong option for users who need both L4 and L7 load balancing in a unified solution.
Current Kubernetes Integrations
- service type LoadBalancer
- kube-proxy replacement with eBPF
- Ingress Support
- Kubernetes Gateway API
- HA capable Egress for Kubernetes
- Kubernetes Network Policies (in-progress)
Telco-Cloud with loxilb
When deploying telco-cloud environments using cloud-native network functions (CNFs), loxilb can serve as a Service Communication Proxy (SCP). SCP is a component defined by 3GPP to optimize communication between telco microservices in cloud-native deployments. You can read more about this use case here.
Telco-cloud workloads require load balancing and protocol-aware communication across a wide range of interfaces and standards such as N2, N4, E2 (ORAN), S6x, 5GLAN, GTP, and others. Each interface brings its own set of challenges, which loxilb is designed to address. Examples include:
- N4: Requires session-aware intelligence at the PFCP layer
-
N2: Requires NGAP protocol parsing
Related Blogs
-
S6x: Requires Diameter protocol load balancing with SCTP multi-homing
Related Blog
-
MEC (Multi-access Edge Computing): May require uplink classifier (UL-CL) support
Related Blog
-
Mission-critical apps: May require hitless failover and zero-downtime behavior
- E2 (ORAN): May require SCTP load balancing integrated with OpenVPN
- SIP (Session Initiation Protocol): Needed for enabling cloud-native VoIP
- N32: Requires support for SEPP (Security Edge Protection Proxy)
loxilb’s deep protocol awareness and ability to operate efficiently in Kubernetes environments make it a strong fit for modern telco-cloud deployments.
Why choose loxilb?
- Performs much better compared to its competitors across various architectures — Single-Node Performance, Multi-Node Performance, Performance on ARM, Short Demo on Performance
- Utilizes eBPF, making it both
flexibleandcustomizable - Advanced
quality of servicefor workloads (per LB, per endpoint, or per client) - Works with
anyKubernetes distribution/CNI (k8s / k3s / k0s / kind / OpenShift + Calico, Flannel, Cilium, Weave, Multus, etc) - Kube-proxy replacement with loxilb allows
simple plug-inwith any existing or deployed pod-networking software - Extensive support for
SCTP workloads(with multi-homing) on Kubernetes - Dual stack with
NAT66, NAT64support for Kubernetes - Kubernetes
multi-clustersupport (planned 🚧) - Runs in
anycloud (public cloud / on-prem) orstandaloneenvironments
Overall Features of loxilb
- L4/NAT Stateful Load Balancer — Supports NAT44, NAT66, NAT64 with One-ARM, FullNAT, DSR, and more. Protocol support includes TCP, UDP, SCTP (with multi-homing), QUIC, FTP, TFTP
- High Availability — Built-in clustering with support for hitless failover, Maglev, and CGNAT-style redundancy
- Scalable Endpoint Health Probes — Cloud-native friendly liveness checks for large-scale workloads
- Integrated Security — Stateful firewall capabilities with support for IPsec and WireGuard tunnels
- Optimized Kernel Features — High-performance implementations for conntrack, QoS, and other Linux networking functions. Learn more
- IPVS Compatibility — Full support for IPVS-based policies with automatic inheritance
- Layer 7 Proxy Support — Policy-driven HTTP proxying for HTTP/1.0, 1.1, and 2.0
Components of loxilb
- Control Plane (Go) — Control plane built in Go for reliability and modularity
- Data-Path (eBPF) — High-performance, scalable datapath powered by eBPF
- Routing Stack — Integrated BGP support using a built-in GoBGP based implementation
- Kubernetes Integration — A native Kubernetes agent, kube-loxilb, written in Go for seamless service discovery and synchronization
Architectural Considerations
-
Understanding loxilb modes and deployment in Kubernetes with kube-loxilb
A deep dive into how loxilb operates in different deployment modes, and how thekube-loxilbagent enables seamless integration with Kubernetes. -
Understanding High-Availability with loxilb
Covers clustering options, failover strategies, and how loxilb ensures resilient service delivery in high-availability environments.
Getting started with different K8s distributions & tools
loxilb as ext-cluster pod
- K8s : loxilb ext-mode
- K3s : loxilb with default flannel
- K3s : loxilb with calico
- K3s : loxilb with cilium
- K0s : loxilb with default kube-router networking
- EKS : loxilb ext-mode
loxilb as in-cluster pod
- K8s : loxilb in-cluster mode
- K8s : loxilb in-cluster mode with cilium
- K3s : loxilb in-cluster mode
- K0s : loxilb in-cluster mode
- MicroK8s : loxilb in-cluster mode
- EKS : loxilb in-cluster mode
- RedHat OCP : loxilb in-cluster mode
- K8s : loxilb in-cluster with calico/multus
loxilb as service-proxy
loxilb as Kubernetes Ingress
loxilb as Kubernetes Egress
loxilb in standalone mode
Advanced Guides
- How-To : Service-group zones with loxilb
- How-To : Access end-points outside K8s
- How-To : Deploy multi-server K3s HA with loxilb
- How-To : Deploy loxilb with multi-AZ HA support in AWS
- How-To : Deploy loxilb with multi-cloud HA support
- How-To : Deploy loxilb with ingress-nginx
- How-To : Run loxilb in-cluster with secondary networks
- How-To : Kubernetes virtual cluster setup with k3k and loxilb
- How-To : Kubernetes service sharding with loxilb
- How-To : loxilb L4/L7 Load-Balancing with Kubernetes Gateway API
- How-To : Use proxy protocol v2 with loxilb
Knowledge-Base
- What is eBPF
- What is k8s service - load-balancer
- Architecture in brief
- Code organization
- eBPF internals of loxilb
- What are loxilb NAT Modes
- loxilb load-balancer algorithms
- Manual steps to build/run
- Debugging loxilb
- loxicmd command-line tool usage
- Developer's guide to loxicmd
- Developer's guide to loxilb API
- HTTPS guide for loxilb API
- OAuth2 guide for loxilb API
- API Reference - loxilb web-Api
- Performance Reports
- Development Roadmap
- Contribute
- System Requirements
- Frequenctly Asked Questions- FAQs
Blogs
- Building a resilient EKS Cluster with in-cluster auto-scaled LoxiLB
- K8s - Elevating cluster networking
- eBPF - Map sync using Go
- K8s in-cluster service LB with LoxiLB
- K8s - Introducing SCTP Multihoming with LoxiLB
- Load-balancer performance comparison on Amazon Graviton2
- Hyperscale anycast load balancing with HA
- Getting started with loxilb on Amazon EKS
- K8s - Deploying "hitless" Load-balancing
- Oracle Cloud - Hitless HA load balancing
- Ipv6 migration in Kubernetes made easy
- Measuring Performance in L4-L7 Load Balancing
- Setup K8s with HA capable egress
Community Posts
- 5G SCTP LoadBalancer Using loxilb
- 5G Uplink Classifier Using loxilb
- K3s - Using loxilb as external service lb
- K8s - Bringing load-balancing to multus workloads with loxilb
- 5G SCTP LoadBalancer Using LoxiLB on free5GC
- Kubernetes Services: Achieving optimal performance is elusive
- LoxiLB: Another Load Balancer
- LoxiLB eBPF deep-dive
Research Papers (featuring loxilb)
- Mitigating Spectre-PHT using Speculation Barriers in Linux BPF
- A Scalable and Fault-Tolerant 5G Core on Kubernetes



